- Use Cases
- By Category
- What is SSPM?
- Top Ten Integrations
Google Workspace

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST - Platform
- Platform Features
- Main Features
- Prevention Features
- Posture By App
- Detection & Response Features
- Remediation
- Integrations

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more - Resources
- Library
- All Resources
- Blogs
- All Blogs

The SSPM Justification Kit
GET THE KIT - Partners
- Tech Partners
 CrowdStrike
CrowdStrike- Business Partners
- Partner Program

Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download - Company


- Use Cases
- By Category
- What is SSPM?
- Top Ten Integrations
Google Workspace

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST - Platform
- Platform Features
- Main Features
- Prevention Features
- Posture By App
- Detection & Response Features
- Remediation
- Integrations

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more - Resources
- Library
- All Resources
- Blogs
- All Blogs

The SSPM Justification Kit
GET THE KIT - Partners
- Tech Partners
 CrowdStrike
CrowdStrike- Business Partners
- Partner Program

Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download - Company
- All topics
- Whitepapers & Reports
- Webinars & Videos
- Analyst Reports
- Solution Briefs / Datasheets

The SSPM Justification Kit
Everything You Need to Explain the Importance of SaaS Security Posture Management and Get Internal Buy-in

SaaS Security in Healthcare: Doctolib Success Story
How the European e-Health Leader Implemented an Agile and Robust SaaS Security Program at Scale

Sécurité SaaS dansl’e-Santé
Comment l’entreprise française, leader en Europe, a mis en œuvre un programme agile et robuste à grande échelle

SaaS Security Beyond Just Misconfigurations
In this interview, Maor Bin, CEO and Co-Founder of Adaptive Shield, discusses the evolving landscape of SaaS Security. He highlights the challenges posed by the security gap resulting from the rapid adoption of SaaS applications and why SaaS security is beyond just misconfiguration management.

Emerging Tech: Gartner® Offers Critical Insights on SaaS Security
Gartner® analysts examine the security of the SaaS ecosystem and have identified some key challenges organizations face in securing their SaaS applications.

SSPM vs CASB Datasheet
Many organizations initially used CASBs to secure their SaaS applications. However, SaaS has far outgrown CASB’s capabilities and a new tool, SSPM, is now vital.

The Annual SaaS Security Survey Report
2025 CISO Plans and Priorities

Securing SaaS Under DORA Regulations
DORA was created by the EU to strengthen the operational resilience of its financial entities. The EU recognized that the digital transformation taking place in the financial services industry place an unprecedented reliance on technology. Within this reliance, SaaS security falls under ICT Risk Management.

The Ultimate SaaS Security Posture Management (SSPM) Checklist
If purchasing an SSPM solution is on your radar, here’s a checklist for what to look out for when evaluating the different options.

Adaptive Shield Solution Brief
What is SaaS Security Posture Management and how does it allow you to make the most of your SaaS security controls.

Closing SaaS Security Gaps Webinar with Netpoleon
Join Joel Ramos from Netpoleon ANZ and Mike Roman from Adaptive Shield as they dive into the world of SaaS security.
Closing SaaS Security Gaps (German Webinar)
SaaS-Anwendungen bilden heutzutage den Kern moderner Prozesse, was Unternehmen dazu verpflichtet, die Sicherheit ihres digitalen Ökosystems zu gewährleisten. Begleiten Sie Christian Ulmer, CISO und Gründer von CySafe, sowie Simon Attia, Customer Success Manager bei Adaptive Shield. Dort tauchen sie tief in die Welt der SaaS-Security ein.

Initiez votre programme de sécurité SaaS avec l’approche SSPM
Joignez-vous à nous pour un Live Webinar présenté par Al Anconina, Country Manager France de chez Adaptive Shield, leader du marché des SSPM en France et par Alexandre Demilly, CEO & Architecte Cloud spécialiste Microsoft chez Wakers.

Reality Check: Identity Security for Human and Non-Human Identities
Don’t let your identities be the weak link. You can proactively defend your SaaS environment by implementing a strong identity security posture. Join Maor Bin as he dives deep into the world of SaaS identity security.

Applying NIST Cybersecurity Framework to Your SaaS Stack
The NIST Framework is essential for organizations interested in hardening security, as it provides a high-level, strategic view of cybersecurity risk. However, the framework hasn’t been adapted to the specific needs of SaaS security. Download this checklist to learn the five functions of the NIST framework and how to apply its principles and best practices […]

2024 SaaS Security Trends and How to Close the Gaps with SSPM
Join Matthew Rosenquist, CISO and renowned cybersecurity advocate, and our own Maor Bin, CEO and co-founder of Adaptive Shield, as they dive into the security implications of massive deployment of SaaS apps, and new tactics to prevent SaaS security lapses.

The Business Imperative of SaaS Security Posture Management
David Neuman, senior analyst at TAG Cyber, looks at how the rise of SaaS applications has fundamentally changed the way businesses use software. SaaS applications make up 70% of all business software applications, containing files, sensitive employee and customer data, financial records, and more.

The Hidden Risks in Your SaaS Applications
David Neuman, senior analyst at TAG Cyber, examines the security risks that come with a move to SaaS applications. He explores all the major attack vectors, and encourages organizations to take a proactive approach to mitigate those risks.

The Total Economic Impact™ of Adaptive Shield’s SSPM Solution
The 2024 Forrester Consulting TEI study is designed to determine this ROI includes elements of SaaS Security score, and operational efficiency against costs of a data breach, based on data from the customer experience of a global corporation.

Frost & Sullivan’s 2023 Global Technology Innovation Leadership Award
Adaptive Shield is honored to be recognized as the 2023 tech leader of SaaS Security Posture Management (SSPM) by Frost & Sullivan. The award recognizes the quality of the Adaptive Shield solution and the customer value enhancements it enables.
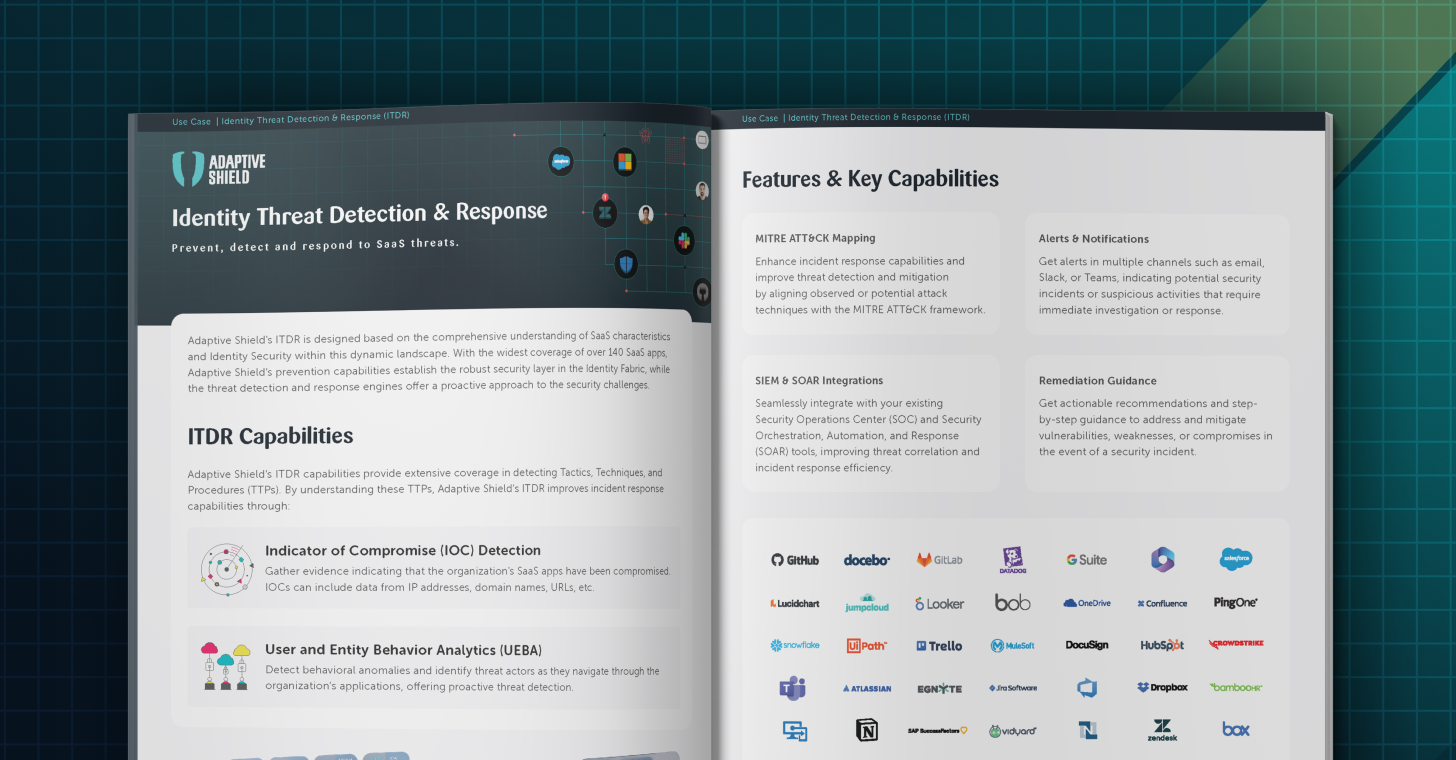
Identity Threat Detection & Response: Solution Brief
Adaptive Shield’s ITDR is designed based on the comprehensive understanding of SaaS characteristics and Identity Security within this dynamic landscape. With the widest coverage of over 140 SaaS apps, Adaptive Shield’s prevention capabilities establish the robust security layer in the Identity Fabric, while the threat detection and response engines offer a proactive approach to the […]

SaaS-to-SaaS Access: Solution Brief
With Adaptive Shield, you can see how many 3rd-party apps are connected to your SaaS apps, the names of each app, and their risk level based on granted scopes. The security team can see which users authorized the app, the impact removing the app will have, and the app installations, enabling them to make a […]

Device-to-SaaS Risk: Solution Brief
When employees access company data using a device with poor security hygiene, they put data at risk. Adaptive Shield integrates with leading endpoint security tools and SaaS app user login data to create a device inventory that delineates every device that accessed the SaaS stack and the user who used the device. Security professionals gain […]

Identity Security Posture: Solution Brief
Every user identity is a potential entrance into the SaaS application. Adaptive Shield focuses on strengthening organizations’ rich identity fabric, preventing unauthorized users from accessing corporate SaaS applications. With Adaptive Shield, you can oversee all identity-based access to apps, provide security teams with full visibility into their users, and ensure sufficient protections are in place […]

Misconfiguration Management: Solution Brief
With Adaptive Shield, every configuration in the SaaS stack is tracked in a centralized location, enabling both business users and security professionals to see failed security checks itemized by severity levels, app security scores, affected users, impacted compliance, and remediation steps needed to improve the application’s security posture.

Offboarding Users from Your SaaS Stack in 7 Steps
From reducing risk to protecting against data leakage, there are no less than five security reasons to make sure you know your users in the coming year. This e-book outlines the steps organizations should take to simplify deprovisioning, and recommends tools to automate the process.

SaaS Security Trends and Your 2024 Strategy – Stay Ahead of the Game
The democratization of IT is in full swing, being led by business units purchasing and securing cloud-based SaaS apps. With this joint responsibility, security teams are being relegated to the role of governors instead of controllers, guiding the SaaS application business owners on how to practice security.

Kickstarting Your SaaS Security Program Webinar
In today’s digital landscape, safeguarding your organization’s applications and data within SaaS platforms is paramount. Yet, the path to implementing an effective SaaS security program is not always straightforward.

Identity Threat Detection and Response (ITDR) – Rips in Your Identity Fabric
Corporate SaaS applications are an attractive target for threat actors. When access is compromised, the data within applications can be quickly exfiltrated and monetized. Most threat detection and identity management methods don’t provide enough protection.

Kickstarting Your SaaS Security Program
This guide explores the challenges inherent in SaaS security, shows why SaaS security became a top priority for most CISOs, and provides nuts-and-bolts guidance on how to establish the foundations of a strong SaaS security strategy.
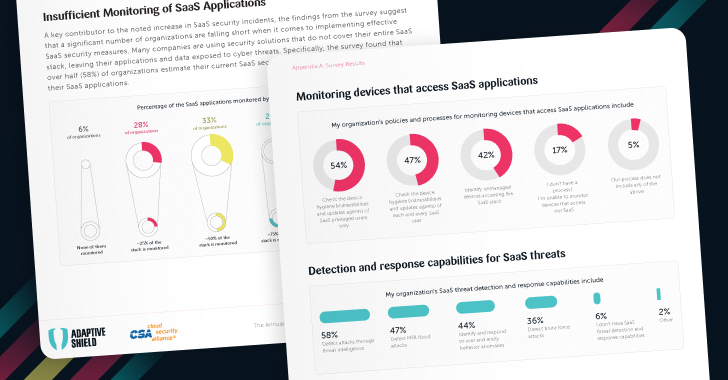
The Annual SaaS Security Survey Report: Plans and Priorities for 2024
Over 55% of security executives report that they have experienced a SaaS security incident in the past two years — a significant jump from last year’s survey. Understanding the state of SaaS security and what steps organizations are taking is therefore essential for organizations to protect themselves from SaaS risks.

Schrödinger Increases SaaS Security Posture by 300% in Only 4 Months
As Schrödinger expanded, they increased their reliance on business-critical SaaS applications. The security team had used CASBs in previous roles but were frustrated by the high volume of false positives CASBs generated. The team decided to dive into the security controls of each SaaS application.

Inside the High Risk of 3rd Party SaaS Apps
Are you aware of the potential risks that come with third-party app access to your company’s SaaS apps? While it may boost productivity and enable remote work, it also significantly increases your organization’s vulnerability to cyberattacks. In fact, security teams and organizations struggle to keep track of the number of connected apps and quantify the […]

How to Tackle the Top SaaS Security Challenges of 2023
In this webinar, we delve into the core of SaaS security and shed light on the biggest challenges SaaS users will encounter in 2023. Maor Bin, CEO & Co-founder at Adaptive Shield provides actionable insights on how an SSPM can help solve these challenges and protect valuable data.

2023 SaaS-to-SaaS Access Report
Any app that can improve business operations is quickly added into the SaaS stack. However, employees don’t realize that this SaaS-to-SaaS connectivity, which typically takes place outside the view of the security team, significantly increases risk. In an effort to better understand this challenge, Adaptive Shield’s researchers analyzed anonymized data from hundreds of tenants to […]

Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management
Forrester interviews customers across different organizations who have implemented a SaaS security posture management (SSPM) solution to create a consolidated report of industry perspective.

SaaS Security Trends, Challenges and Solutions for 2022
Join these two security experts as they discuss insights from the 2022 SaaS Security Survey Report, highlighting the classic challenges as well as the next trends, and the technology organizations can implement to secure their SaaS stack.
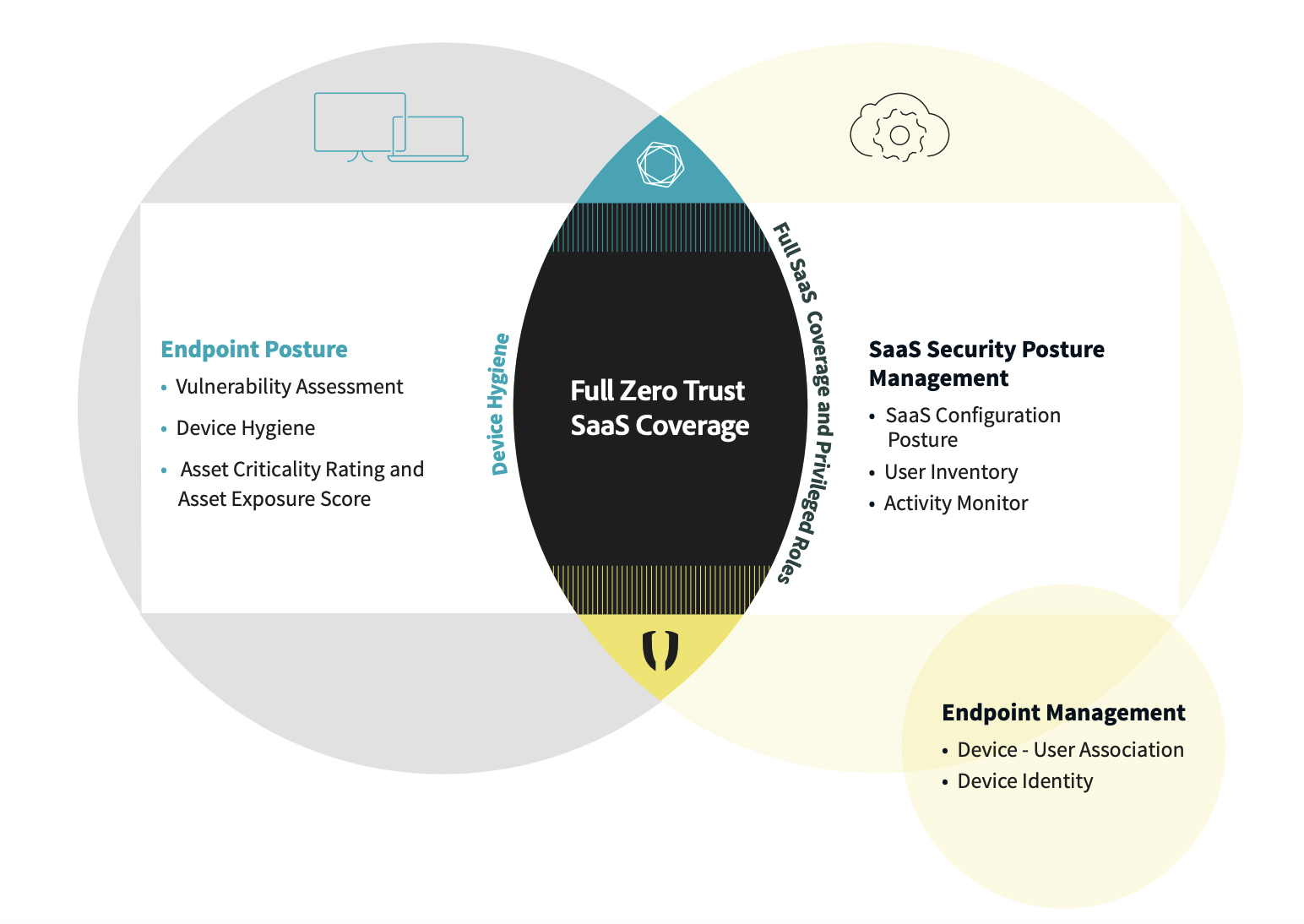
Tenable & Adaptive Shield: Discover Your SaaS Security and Device Posture
By correlating Tenable’s rich endpoint telemetry and ACR and AES scoring within the Adaptive Shield’s SaaS security posture technology, your security team will gain unprecedented context and visibility to easily see and manage the risks that stem from SaaS users and their associated devices.

The SaaS RootKit: A New Attack Vector for Hidden Forwarding Rules in O365
Researchers detected a new SaaS vulnerability within Microsoft’s OAuth application registration. Through this vulnerability, anyone can leverage Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. This talk will demo the OAuth registration process in Microsoft as well as the use of the new vulnerability.

2022 Gartner® Cool Vendors™ in Application Security Report
We are excited to announce that Gartner has named us a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications. Read more to get all the details.

On The Radar: An Omdia Report by Senior Principal Analyst Rik Turner
Accelerated cloud adoption, as well as the burgeoning threat landscape and the ongoing shortage of skilled security professionals, is driving the cybersecurity world towards more proactive approaches, after a decade in which reactive (detect and respond) ones held sway.

2022 SaaS Security Survey Report
Our 2022 SaaS Security Survey Report, in collaboration with CSA, dives into how CISOs today are managing the burgeoning SaaS app attack surface and the steps they are taking to secure their organizations.

Taking a Proactive Approach to Securing SaaS
The explosion in the number and variety of SaaS apps available to enterprises creates both opportunities and challenges. With the growing SaaS stack, the potential attack surface for bad actors also increases. It is the cybersecurity department’s mission to ensure that their organization’s security hygiene remains intact. Join this webinar to learn all about the […]

Crowdstrike & Adaptive Shield: Build a Zero – Trust SaaS Security Posture
A Holistic Solution to Gain Control over Your SaaS Security, Users and Devices. Adaptive Shield, the market-leading SaaS Security Posture Management (SSPM) solution, has partnered with CrowdStrike, a leader in Endpoint Detection and Response (EDR), to create a solution that provides an enhanced SaaS Security assessment.

Prioritizing Your Security Vulnerabilities and Misconfigurations
Maor Bin joins the Teiss Talk team to discuss security vulnerabilities and misconfigurations along with Jenny Radcliffe, Professor Leandros Maglaras and Andrea Manning

Adaptive Shield and Okta: Fortified SaaS Security and Identity and Access Management
Joint Offering Ensures That Authorized Users Can Safely Access Any SaaS App Without Exposing Companies to Unnecessary Risks

Shifting Away from Legacy Authentication Protocols in Microsoft 365
In order to enable a smooth transition from these legacy protocols to a modern environment, Adaptive Shield has created a step-by-step guide to help you reduce risk and reinforce your organization’s M365 security.

Attacking and Defending the Microsoft Cloud (eBook)
As companies recognize the many benefits that cloud and software-as-a-service (SaaS) solutions provide, many organizations have shifted or are in the process of shifting operations into the cloud.For companies using Microsoft, this includes a move to the Microsoft Cloud, including Azure ActiveDirectory (AD) and Microsoft Office 365.

Black Hat Fast Chat with Maor Bin
Adaptive Shield CEO, Maor Bin, answers why it’s a challenge to secure the SaaS app estate.

The 2021 SaaS Security Survey Report
To understand how teams are currently dealing with their SaaS security posture, and what their main concerns are in handling SaaS tools, we surveyed 300 InfoSecurity professionals from North America and Western Europe, in companies of 500+ employees.

CISO/Security Vendor Relationship Podcast Talks About SaaS Security Posture and More
A recap of the CISO/Security Vendor Relationship podcast, hosted by David Spark and Mark Johnson. sponsored guest, TIAA’s Travis Hoyt.

The CISO Gambit: Staying a Step Ahead in SaaS Security Posture
A Black Hat Webcast by Adaptive Shield with Maor Bin.

Attacking and Defending the Microsoft Cloud (Webinar)
The allure of the “Cloud” is indisputable. Organizations are moving into the cloud at a rapid pace. Even companies that have said no to the Cloud in the past have started migrating services and resources. The Cloud is a new paradigm, and the rapid update pace makes it difficult to keep up, especially when it […]

Adaptive Shield & Snowflake: All your SaaS Security Controls on your Data Cloud
Adaptive Shield and Snowflake have partnered up to introduce a solution that allows organizations to manage their SaaS security posture using Snowflake security data lake.










