Let's Get Technical
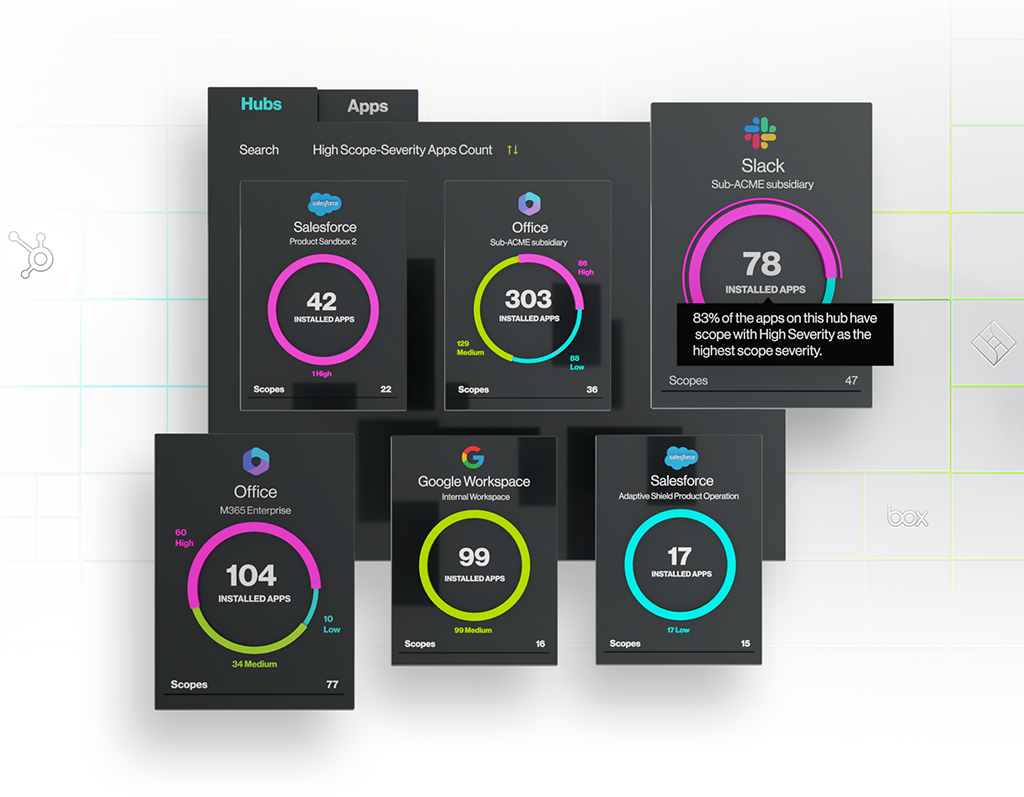
Adaptive Shield detects all 3rd party apps connected to each business-critical SaaS application including M365, Google Workspace, Salesforce, Github, your IDP, and more. This includes information on their risk-severity level and the scopes granted, enabling you to automatically block or revoke access based on your policy.
Main capabilities:
Vendor name and verification status
Installation date of the app
Description of the application
Users who gave consent to the app
Scopes granted to the app and their risk severity
Last used date, including a summary of the occurrences in which the apps actualized the scopes
Auto-remediation based on policy
How This Can Help You
Visibility and Full Management of Connected Apps
Malicious App Threat Detection
Manage Access
Identify those high-risk or irrelevant dormant connected apps and automatically/manually adjust access