Today we’ve announced our breakthrough Identity Threat Detection & Response (ITDR) platform for SaaS environments. Since entering this space a year ago, we’ve already become a leader in the field, implementing the solution in hundreds of enterprise customer environments.
Adaptive Shield will demonstrate its new ITDR platform and award-winning technology at booth #1268 during Black Hat USA, from August 7-8, 2024, showcasing its capabilities with the most complex threat detection use cases and campaigns seen in the wild.
The recent Snowflake breach served as a wake-up call for the SaaS industry. On May 27, a threat group announced the sale of 560 million stolen records from targeted attacks on single-factor authentication users in Snowflake. This event, which continues to make headlines, follows a series of significant breaches in SaaS applications over recent months.
“The Snowflake breach is a classic example of a SaaS security event that could have been prevented or, if not, detected. Organizations must recognize the shared SaaS security responsibility model, in which SaaS vendors provide native security controls, but it is ultimately the organization’s duty to actively ensure these controls are implemented,” said Maor Bin, co-founder and CEO of Adaptive Shield. “Major incidents like this could easily be prevented with proper monitoring and hardening tools. Beyond prevention, which is fundamental to SaaS security, having threat detection and response capabilities tailored for SaaS applications would have identified the Indicators of Compromise (IoCs) and halted the attack at the perimeter.”
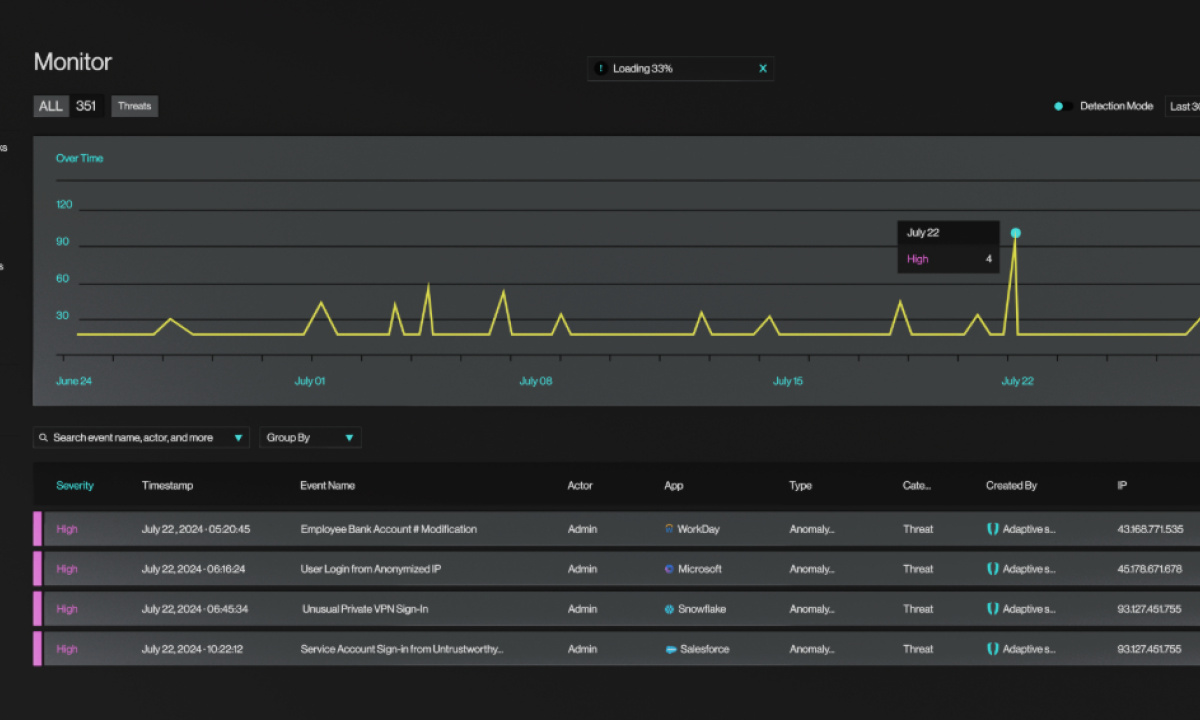
Adaptive Shield’s ITDR platform works alongside the company’s prevention SaaS Security Posture Management (SSPM) platform and enables enterprises to proactively cover the breadth of attack vectors within the SaaS ecosystem. Identity-centric threats can originate from misconfigured settings, human and non-human identities, and compromised SaaS user devices. These threats manifest in various forms, such as account takeovers, unintended publicly available links, malicious applications, and more. Real-life sophisticated campaigns detected by Adaptive Shield customers include:
- Threat actors taking over credentials in a payroll & HR management system and changing employee bank account details to transfer their salary to a different account.
- A partially deprovisioned former employee accessed and downloaded very sensitive data. This occurred due to misconfigurations within a highly complex operational platform.
- Detection of lateral movement from a disabled MFA demo account into production via OAuth, as a malicious app, directly into employee mailboxes.
- Access to public links in the CRM, intended for data sharing. While these public links were password protected, had expiration dates, and usage tracking, they were still accessible to unauthorized users.
- Account hijacking through user compromised user devices.
“Current ITDR solutions primarily address endpoint and on-premises Active Directory protection, but they do not cover the intricate SaaS environment. Addressing SaaS-related threats demands deep expertise and can be achieved only by cross-referencing and analyzing suspicious events in context from multiple sources, ensuring precise detection of subtle identity-centric threats,” said Gilad Walden, VP Product at Adaptive Shield.



















