How Adaptive Shield Helps Secure Salesforce
Salesforce contains sensitive customer information, and offers different modules that ensure privacy. However, those security features can be overrun by threat actors if the settings within the application are misconfigured.
Adaptive Shield automates reviews of over 125 configurations in Salesforce, ensuring that all configurations are set correctly and alerting users in the event of configuration drifts.
Through these different security checks, you can count on Adaptive Shield to prevent unauthorized access of your Salesforce.
Securing Against Guest Users
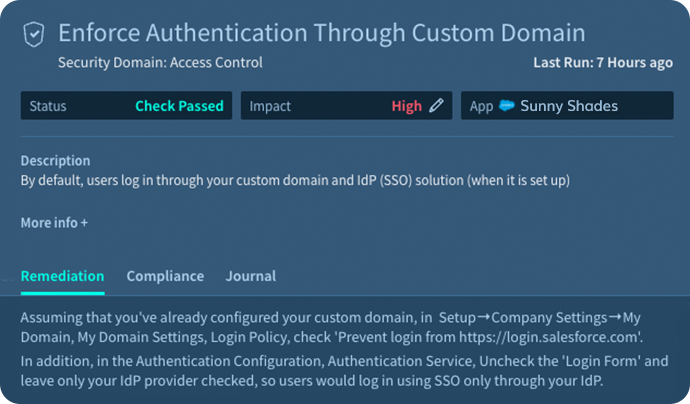
Limit Application Access

Control Public Links

Protect Against Malware

Manage User Passwords

Track Multiple Instances of Salesforce

Govern Permissions and User Access





























 ?>
?>