Let’s Get Technical
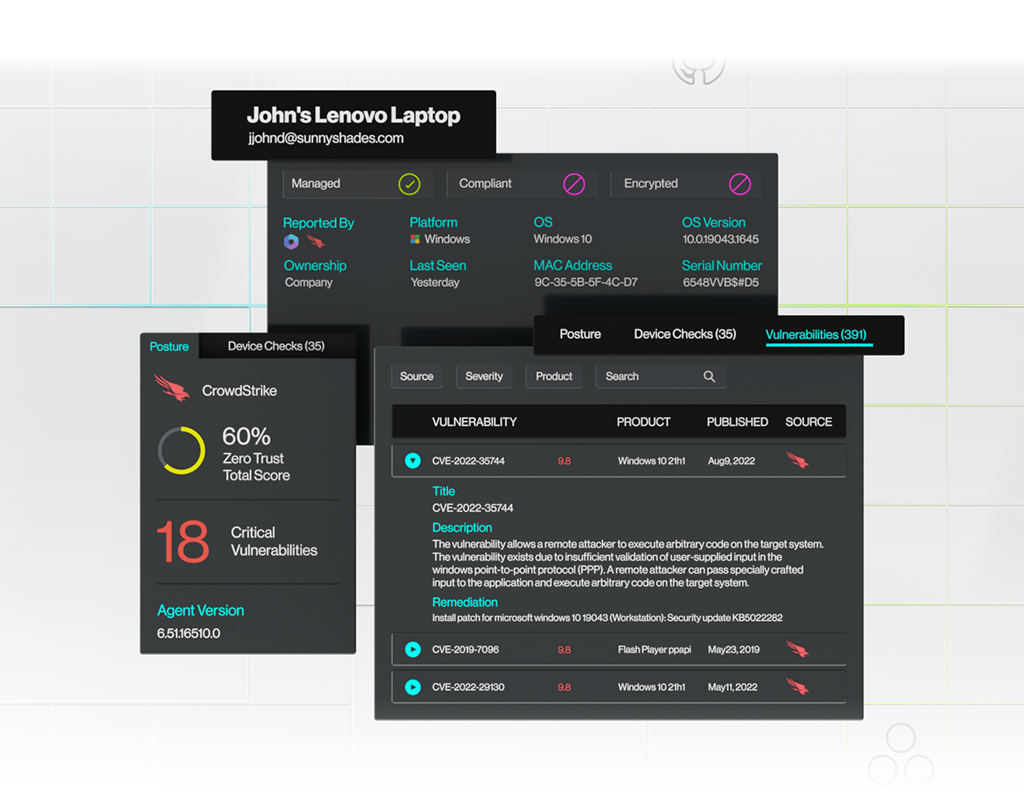
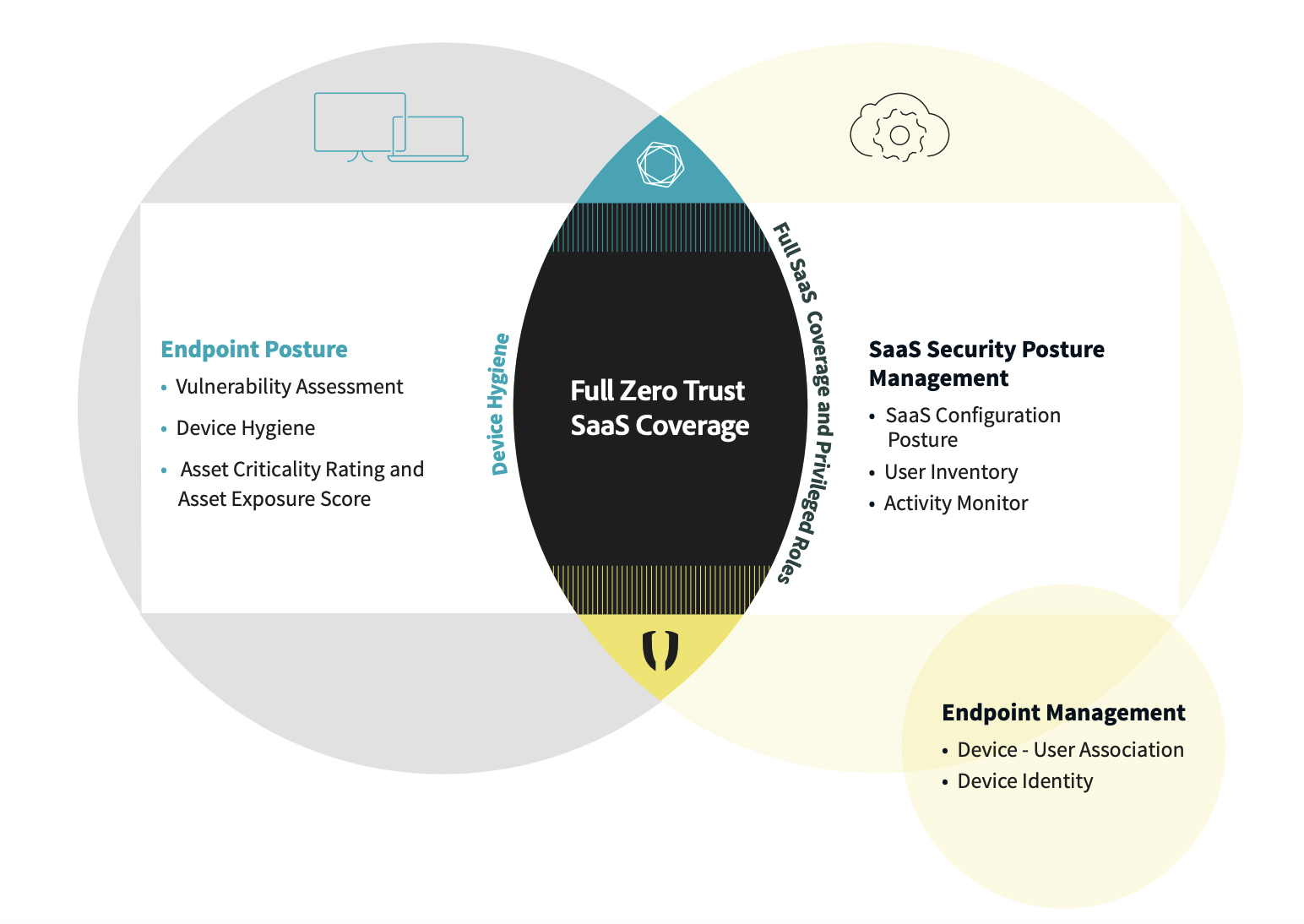
The Adaptive Shield SSPM platform integrates with existing EDR, device management, and vulnerability management platforms for a 360-degree Device-to-SaaS-User picture.
All SaaS-user managed devices listed by owner
Device posture from all endpoint services in place (for example: CrowdStrike – Zero Trust Score, Tenable – AES and ACR, Microsoft Defender – Exposure, risk level, and device value scores)
Details of device platform and OS
Reporting if the device is managed and is compliant
Orphan or dormant devices
User name
SaaS app access
Privileged roles
Other devices associated with the user
See whether the device is within the organization’s MDM and whether it poses any risk
How This Helps You
Privileged Users with Critical Vulnerabilities
Identify high-privileged SaaS users with poor cyber hygiene on their devices, devices that are non-compliant with organizational policies, and unmanaged devices
Device Missing Endpoint Protection Reporter
Create security checks that identify devices that are not reported by the endpoint device